ENS Security course 2020
Lecturer: Clémentine Maurice
Teaching assistant: Guillaume Didier
Contact
For questions on the lectures: clementine.maurice AT irisa.fr
For questions on a project: clementine.maurice AT irisa.fr, or guillaume.didier AT irisa.fr, depending on the tutor.
Lectures
- #1. Introduction (17/09/2020) [PDF]
- #2. Defenses (24/09/2020) [PDF]
- #3. Attacking all the things (01/10/2020) [PDF]
Grading
- Project report due December 4 (11:59am): 50% of your grade
- 3 to 5 pages
- Summarize the context, problem(s) you faced and the method you used
- Project presentations on December 10: 50% of your grade
- 20 minutes presentation + 10 minutes of questions
- Summarize background and the two articles given, explain the aim of your project and the steps you took
- Final report due December 17
- We will ask for corrections if needed, so that we can distribute your reports to the whole class
- You can get up to 2 bonus points if you made significant improvements!
Projects
If you take this class, please form groups of two and send your ordered list of the 7 projects by preference by October 5 (11:59am) at clementine.maurice AT irisa.fr. I will do the assignment for the beginning of the projects on October 8.
Also note that for some projects we are giving you more than two references. It's not to punish you, it's to actually help you ;)
The following projects are available:
#1. Adversarial machine learning
Full description here.
An adversarial attack consists of subtly modifying an original image in such a way that the changes are almost undetectable to the human eye. The modified image is called an adversarial image, and when submitted to a classifier is misclassified, while the original one is correctly classified.
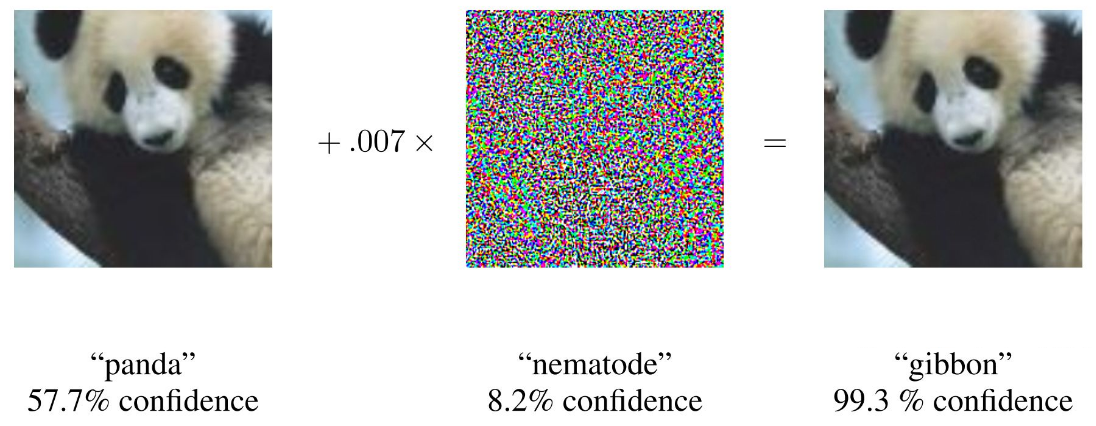
- Ian J. Goodfellow, Jonathon Shlens & Christian Szegedy. Explaining and Harnessing Adversarial Examples. In: ICLR 2015. https://arxiv.org/pdf/1412.6572.pdf
Plus one of the following:
- Nicolas Papernot, Patrick McDaniel, Ian Goodfellow, Somesh Jha, Z. Berkay Celik, Ananthram Swami. Practical Black-Box Attacks against Machine Learning. In Asia CCS 2017. https://arxiv.org/pdf/1602.02697.pdf
- N. Carlini, D. Wagner. Audio Adversarial Examples: Targeted Attacks on Speech-to-Text. In Deep Learning and Security Workshop 2018. https://nicholas.carlini.com/papers/2018_dls_audioadvex.pdf
- Florian Tramèr, Alexey Kurakin, Nicolas Papernot, Ian Goodfellow, Dan Boneh, Patrick McDaniel. Ensemble Adversarial Training: Attacks and Defenses. In ICLR 2018 https://arxiv.org/pdf/1705.07204.pdf
#2. 802.11 fingerprinting
Full description here.
802.11 is a set of standards ratified by the IEEE, describing the characteristics of a Wireless Local Area Network (WLAN), often referred to as “Wi-Fi networks”, i.e., networks based on 802.11 devices. WLANs are widely adopted due to the standardization and interoperability between wireless devices. Yet, the wireless link has to deal with problems that have no analogy in the wired world, such as the unreliability of transmissions and potential attackers in the neighborhood with easy remote interactions. The 802.11 standard is therefore complicated and leads to varying implementations.
Fingerprinting is the action of identifying a device by extracting some externally observable characteristics and using supervised learning. It results in a signature (an identifier for the device being fingerprinted) and a classification of the device. Fingerprinting can be used in a defensive way, to detect and to prevent MAC address spoofing for stations and rogue access points. It can be used in an offensive way as well, by identifying a configuration to target a specific vulnerability and launch a driver-specific exploit. It also raises the question of privacy, as one way to ensure anonymity in 802.11 networks is to change regularly a device MAC address - supposed to be a unique identifier. However, by identifying the device by its observable characteristics, tracking becomes possible without relying on any unique identifier.
- J. Franklin, D. McCoy, P. Tabriz, V. Neagoe, J. V.Randwyk, and D. Sicker. Passive data link layer 802.11 wireless device driver fingerprinting. In Usenix Security, volume 6, 2006. https://www.usenix.org/legacy/events/sec06/tech/full_papers/franklin/franklin.pdf
- C. Matte, M. Cunche, F. Rousseau, M. Vanhoef. Defeating MAC Address Randomization Through Timing Attacks. In: WiSec, 2016. http://papers.mathyvanhoef.com/wisec2016.pdf
#3. Password cracking
Full description here.
Password cracking is the process that consists in recovering passwords from databases. Passwords are usually hashed when stored. The basic idea of a hash function is that it takes an input and produces as output a message of a fixed length. (Good) cryptographic hash functions have the property of being very easy to compute, but extremely difficult to reverse, i.e. given the output, it should not be possible to find the input, and it should also not be possible to find two inputs that produce the same output.
In the real world, passwords are sometimes stored in an unsecure fashion, and users tend to choose weak passwords and to reuse them, all of which has consequences on password cracking.
- Blase Ur, Sean M. Segreti, Lujo Bauer, Nicolas Christin, Lorrie Faith Cranor, Saranga Komanduri, Darya Kurilova, Michelle L. Mazurek, William Melicher, Richard Shay: Measuring Real-World Accuracies and Biases in Modeling Password Guessability. USENIX Security Symposium 2015: 463-481 https://www.usenix.org/system/files/conference/usenixsecurity15/sec15-paper-ur.pdf
- Saranga Komanduri, Richard Shay, Patrick Gage Kelley, Michelle L. Mazurek, Lujo Bauer, Nicolas Christin, Lorrie Faith Cranor, Serge Egelman: Of passwords and people: measuring the effect of password-composition policies. CHI 2011: 2595-2604 https://www.guanotronic.com/~serge/papers/chi11b.pdf
#4. Automated bug finding
Full description here.
Bugs! They are everywhere and everybody is bound to write some in their programming life. Bugs lead to major problems in the reliability, safety, and security of systems both large and small, and it is neither easy nor always feasible to find all bugs by hand. Although it is not a substitute to code review, testing, and program verification, automated bug finding tools can alleviate some of the pain of finding bugs. Numerous techniques have been developed in the past decades, such as fuzzing, dataflow analysis, symbolic execution, model checking, or abstract interpretation. This project should give you a glimpse of this large domain and its current challenges.
- Laszlo Szekeres, Mathias Payer, Tao Wei, Dawn Song: SoK: Eternal War in Memory. IEEE Symposium on Security and Privacy 2013: 48-62 http://www.nebelwelt.net/publications/files/13Oakland.pdf
- Brendan Dolan-Gavitt, Patrick Hulin, Engin Kirda, Tim Leek, Andrea Mambretti, William K. Robertson, Frederick Ulrich, Ryan Whelan: LAVA: Large-Scale Automated Vulnerability Addition. IEEE Symposium on Security and Privacy 2016: 110-121 https://www.andreamambretti.com/files/papers/oakland2016_lava.pdf
And to give you a bit more context about fuzzing:
- Mathias Payer: The Fuzzing Hype-Train: How Random Testing Triggers Thousands of Crashes. IEEE Security & Privacy 17(1): 78-82 (2019) http://nebelwelt.net/publications/files/19SP.pdf
#5. Reverse-engineering
Full description here.
Understanding what a binary program does is essential for security researchers, as often you only have the compiled version of a malware. Analysing and debugging is thus a significant activity of people who are working on malware, or are trying to understand a bug in compiled code, e.g., for security purposes or to understand what your program is getting compiled into and why it is not behaving as you would expect.
This project, conceived as a series of challenges, will expose you to x86 assembly and to various tools used to analyze binaries.
- Asia Slowinska, Traian Stancescu, Herbert Bos: Howard: A Dynamic Excavator for Reverse Engineering Data Structures. NDSS 2011 https://www.cs.vu.nl/~herbertb/papers/howard_ndss11.pdf
- Felix Schuster, Thorsten Holz: Towards reducing the attack surface of software backdoors. ACM Conference on Computer and Communications Security 2013: 851-862 https://www.ei.ruhr-uni-bochum.de/media/emma/veroeffentlichungen/2013/09/18/backdoorDetection-CCS13.pdf
Here are other resources for more background information:
- The Intel assembly primer slides [PDF]
- Carnegie Mellon University's lectures ("machine prog" lectures are the ones relevant for the project): http://www.cs.cmu.edu/afs/cs/academic/class/15213-s18/www/schedule.html
- Computer Systems: A programmer perspective, 3rd edition is also a good reference
- A very complete book on reverse engineering and assembly for beginners for when you want more details on a specific topic: https://beginners.re/RE4B-EN.pdf [EN], https://beginners.re/RE4B-FR.pdf [FR].
- The ultimate reference, Intel Softare Developper manual : https://software.intel.com/content/www/us/en/develop/articles/intel-sdm.html#combined
#6. Crypto in the real world
Full description here.
Cryptanalysis is the process of finding weaknesses in cryptographic systems, and using these weaknesses to decipher the ciphertext without having the secret key. Attacks can target the cryptographic primitive itself (i.e., the mathematical foundations of the algorithm), but more often cryptanalysis targets the usage of this primitive. Indeed, the devil is usually in the details! The interaction between compression and encryption, cipher modes, and protocol negotiation are a few ways attackers can blow up encryption that used primitives that are deemed safe, because they are used inappropriately.
When the iron blast door is attached to a wooden door frame, don’t blow up the door, just break the door frame!
Read this first to familiarize yourself with cryptographic attacks:
- Ben Herzog: Cryptographic Attacks: A Guide for the Perplexed https://research.checkpoint.com/cryptographic-attacks-a-guide-for-the-perplexed/
And here are the two articles to read and summarize for the project presentation:
- Serge Vaudenay: Security Flaws Induced by CBC Padding - Applications to SSL, IPSEC, WTLS... EUROCRYPT 2002: 534-546 https://www.iacr.org/archive/eurocrypt2002/23320530/cbc02_e02d.pdf
- Robert Merget, Juraj Somorovsky, Nimrod Aviram, Craig Young, Janis Fliegenschmidt, Jörg Schwenk, Yuval Shavitt: Scalable Scanning and Automatic Classification of TLS Padding Oracle Vulnerabilities. USENIX Security Symposium 2019: 1029-1046 https://www.usenix.org/system/files/sec19-merget.pdf
#7. Buffer overflows
Full description here.
Out of bound accesses (and writes) to buffer are a recurring issue in computer security, especially for code bases written in C based language. In this project we explore how to exploit buffer overflows (that is writes past the end of buffers) in order to hijack the control flow of the program.
This project will involve learning about the program stack memory layout, assembly, and in the last part memory allocator structures.
Read this seminal publication first to familiarize yourself with buffer overflows:
- Aleph One: Smashing The Stack For Fun And Profit. Phrack 49, 1996 http://phrack.org/issues/49/14.html
Here are the two articles to read and summarize for the project presentation:
- Ryan Roemer, Erik Buchanan, Hovav Shacham, Stefan Savage (2012). Return-oriented programming: Systems, languages, and applications. ACM Transactions on Information and System Security (TISSEC), 15(1), 2. https://hovav.net/ucsd/dist/rop.pdf
- Laszlo Szekeres, Mathias Payer, Tao Wei, Dawn Song: SoK: Eternal War in Memory. IEEE Symposium on Security and Privacy 2013: 48-62 http://www.nebelwelt.net/publications/files/13Oakland.pdf
More publications about attacks on the heap for the last part of the project (to read in order):
- anonymous: Once upon a free(). Phrack 57, 2001 http://phrack.org/issues/57/9.html
- Michel "MaXX" Kaempf: Vudo - An object superstitiously believed to embody magical powers. Phrack 57, 2001 http://phrack.org/issues/57/8.html
- jp: Advanced Doug lea's malloc exploits. Phrack 61, 2003 http://phrack.org/issues/61/6.html
And other resources for more background information:
- The Intel assembly primer slides [PDF]
- Carnegie Mellon University's lectures ("machine prog" lectures are the ones relevant for the project): http://www.cs.cmu.edu/afs/cs/academic/class/15213-s18/www/schedule.html
- Computer Systems: A programmer perspective, 3rd edition is also a good reference
- A very complete book on reverse engineering and assembly for beginners for when you want more details on a specific topic: https://beginners.re/RE4B-EN.pdf [EN], https://beginners.re/RE4B-FR.pdf [FR].
- The ultimate reference, Intel Softare Developper manual : https://software.intel.com/content/www/us/en/develop/articles/intel-sdm.html#combined
#8. Sandbox escape
Full description here.
Sandboxes are a good way to limit damage that can be caused by someone exploiting a bug in a trusted program or to prevent an untrusted program from harming a system.
But building sandboxes is hard! This project will allow you to break a fake sandbox component and think about how to build a better one.
- Tal Garfinkel: Traps and Pitfalls: Practical Problems in System Call Interposition Based Security Tools. NDSS 2003. https://www.ndss-symposium.org/wp-content/uploads/2017/09/Traps-and-Pitfalls-Practical-Problems-in-System-Call-Interposition-Based-Security-Tools-Tal-Garfinkel.pdf
- Tal Garfinkel, Ben Pfaff, Mendel Rosenblum: Ostia: A Delegating Architecture for Secure System Call Interposition. NDSS 2004 https://benpfaff.org/papers/ostia.pdf